Blog
Knowing that Microsoft Office is one of the most popular and widespread software suites on the planet, cyber-criminals and hackers seeking likely victims will often make Office documents and applications the focus of their attempts to gain access to external systems, or generally wreak havoc. Much of this activity relies on scripts containing malicious code, which can call up a variety of actions.
The Nature Of The Threat
According to Cisco’s 2021 Cyber Security Threat Trends report, 86% of organisations surveyed had at least one user attempt to connect to a phishing website while users in 70% of organisations were served with malicious ads. Despite being an old trick, phishing is a popular approach because it is simple and effective. It targets the security weakest link - the user. Phishers frequently impersonate reputable people in electronic communications. That's probably why it accounts for 90% (that's not a typo) of data breaches, according to Cisco.
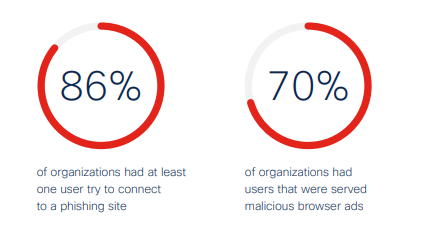
(Image source: Cisco.com)
Such attacks exploit the natural knee-jerk reaction to tempting offers or threatening situations. In response to an irresistible offer or threat, phishing emails or text messages typically invite a prospective victim to follow links to a booby-trapped website or to open a document containing malicious code.
For users of Microsoft products, malicious software or malware may try to infect a victim’s computer by calling up executable files and scripts used in Office apps or webmail. These may attempt to download or run files designed or supplied by the hacker. Malicious scripts can give them an entry point to a personal system or corporate network, or enable them to corrupt existing files and applications.
Enterprise system administrators often have a multitude of Microsoft Office users to assist and oversee, making the issue of dealing with external threats, particularly challenging. The following techniques and recommendations can help.
Identify Your Users And Your Office Functionality Needs
You first need to identify who in your organization is actually using Microsoft Office, in terms of names and numbers. You must then establish what kind of office implementation each of these users requires. In some cases, the user may not require the full functionality of an Office Suite, or need access to all of the tools available.
Use An Appropriate Microsoft Office Deployment Method
Not every user in an Office 365 installation has to have the same setup. For enterprise users, it’s possible to mix and match different versions of Microsoft licensing, inside your Office 365 deployment. For example, users with limited functionality requirements may be able to work from a web-based version of Office that isn’t installed on your system directly. This can also make security deployment easier, as web installations can be run in a “sandbox” mode that keeps them separate from the rest of your network.
Your enterprise hierarchy may make higher profile executives within your organization a more tempting target for hackers. Likewise, security monitoring may reveal that certain individuals at various levels of the company are being targeted by phishing attempts more frequently than others. Users like these may benefit from an Office license with greater security protections and more sophisticated tools.
For users in your organization who don’t require the full collaborative functionality of Microsoft Office, it may even be desirable to use an alternative software suite. Teamwork and document sharing can often be accomplished by other methods such as read-only PDF files, online forums, or web-based forms.

Use Macro And Script Blocking Techniques
Though intended to automate routine functions and make life easier for Office users, macros have rightly gained a reputation as gaping security holes in any system running Microsoft software. Scripting attacks are most often perpetrated through malicious macros that call up actions favourable to the hacker.
It’s worth considering putting restrictions on the running of macros for this reason. Most users don’t actually need to employ advanced features like macros and can get by with a basic Office installation. Any users who do have good reasons for running macros to increase their productivity can be approved for their deployment, and more easily monitored.
If your organization has a traditional domain infrastructure, you can limit the use of Office macros with Group Policy. Versions of Microsoft’s application suite as far back as Office 2010 possess the ability to block macros.
Microsoft recently moved to change the default behaviour of Office applications by blocking macros in files downloaded from the internet as shown in the image below.
![]()
(Image source: Microsoft.com)
The learn more button takes users to an article about the security risk of macros and best practices to protect yourself from scripting attacks. This change will also be rolled back to previous Office versions.
Organisations should update their Internet policies to block macros running in Office files. This prevents users from accidentally opening internet files containing macros.
Use Spam And Email Filtering
Messages and emails are the hacker’s preferred vector for phishing and scripting attacks. So preventing those communications from getting through in the first place makes good sense. You should use spam and email filtering tools to scan and approve messages before users get a chance to open them.
In fact, because of the use of filtering mechanisms, more sophisticated attackers are abandoning attached documents as a means of delivering malicious code, and hosting their scripts in the cloud.
Use Security Software
The increasing ingenuity of script-based attacks requires organizations to adopt more sophisticated security measures and software solutions.
Microsoft recently released a new Microsoft 365 E5 subscription feature called Safe Documents. This service checks Excel, PowerPoint, and Word documents against known risks and threat profiles, before a user can open them.
If you have an active Microsoft 365 E5 license, you can enable the feature as follows:
l Go to the Microsoft 365 Defender portal
l Go to Email & Collaboration
l Go to Policies & Rules
l Click Threat policies
l Click Safe Attachments in the Policies section
l In Global settings, verify the Turn on Safe Documents for Office clients and Allow people to click through Protected View even if Safe Documents identifies the file as malicious settings.
l Click “Save,” to finish.
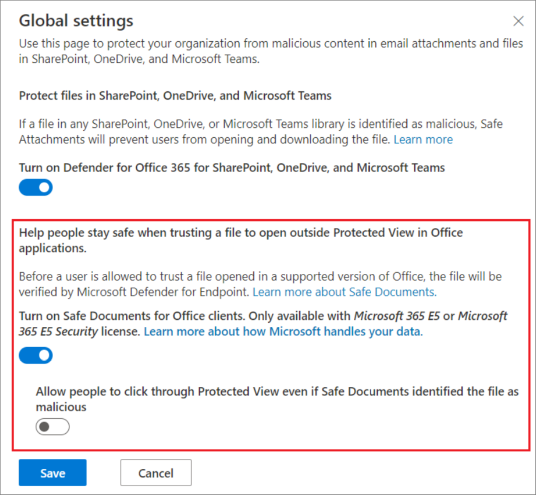
(Image source: Microsoft.com)
Application Guard for Office 365 Pro Plus is another service, which comes with Microsoft 365 E5 or Microsoft 365 E5 Security. Application Guard puts Office in a sandbox environment so that malicious scripts or documents can’t escape into the wider office network or operating system.
Microsoft Defender Advanced Threat Protection (Microsoft Defender ATP) uses what the company calls “attack surface reduction rules” to help prevent behaviours that malicious scripts and malware often use to infect computers with malicious code.
Rules are available for computers running Windows 10, versions 1709 and 1803 or later, Windows Server, version 1803 (Semi-Annual Channel) or later, or Windows Server 2019. To use the entire feature set of attack surface reduction rules, you’ll need a Windows 10 Enterprise license.
If you're using audit mode, you can query Microsoft Defender ATP data by using Advanced hunting. Audit mode provides features to help you understand how attack surface reduction rules could affect your environment. An example query might look like this:
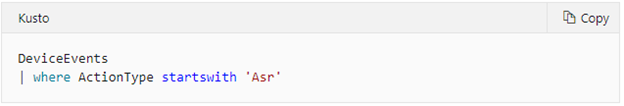
(Image source: Microsoft.com)
Introduce Security Awareness Training And Anti-Phishing Best Practices
Finally, no cyber-security initiative is complete without an associated program of security awareness training and best practices. For scripting attacks on Microsoft Office, these should include email etiquette and anti-phishing measures, as well as letting end-users know the proper procedures for responding to alerts and prompts from their security software.
Add a comment:
Categories
Want better qualified leads for your business?
Latest Blogs
Up to date with whats going, check out our latest blogs
29-03-2023 -
Artificial intelligence has been hitting the headlines in a big way since the end of 2022. Once a rather nebulous concept in the minds of the public, more likely to conjure images of killer science-fiction robots than any real-world application, the release of advanced chatbot application ChatGPT has brought AI into the mainstrea
28-07-2022 -
Introduction
You’re probably familiar in some way with the term “content marketing.” Yet you may be wondering exactly what it is -- and how it’s relevant to you, as a technology company.
07-07-2022 -
Competition is squeezing the bottom line. Inefficient marketing has handicapped the top line. Stuck in between, managed service providers need an efficient, productive, and cost-effective MSP (Managed Service Provider) content marketing strategy to jumpstart business growth.
We’ve been using The Inky Squid for a while now and Martin and his team have been an invaluable extension to our marketing team. As a small company, our need for help with content development is critical. The quality and detail of the articles they’ve written has been impressive. They’re able to write spot-on articles about an extensive variety of technical topics we request. They’re extremely responsive and the turnaround time for projects has been fantastic. We plan to have a long-term relationship with them.
Beth Powell, Expeed Software
The Inky Squid has been a provider of excellent material for our blog for many years. They have always been responsive to our requests and feedback. Highly recommended!
Doug Nebeker, Power Admin
At net2phone, we have been using The Inky Squid for content writing for a few years and love the service we receive. They produce quality and insightful content with quick turnaround times that helps us maintain an active blog and social media presence for our partners and our customers! The writers are knowledgeable, professional, and fast and I'd recommend their services to anyone looking for help with their content marketing strategies.
Denise Darienzo, net2phone
The Inky Squid is a nice team of marketing experts that quickly and effectively respond to the customer's demands. Their campaigns have a personal touch based on the customer's aesthetic; they're appealing to the eye, informative, and result in good engagement. We're happy with the collaborations we've had so far.
Viktoriya Gorod, Starwind Software
I highly recommend The Inky Squid to anyone looking to outsource or complement their content creation program. Their articles are well researched, interesting to read, and have helped us grow our audience. The quality of their work is outstanding, they are very dependable and I can't say enough good things about this company and their work!
Bill Lewis, New Offerings








